Understanding the Abacus Platform
Before diving into RBAC (Role-Based Access Control), it's important to understand the two primary domains of the Abacus Platform:
Developer Platform
URL: abacus.ai/app
This is the core development environment where users can:
- Build Chatbots
- Create predictive modeling use cases
- Set up connectors
- Perform other development tasks
External Chat UI / Super Assistant
URL: <customer-domain>.abacus.ai/chatllm or apps.abacus.ai for non enterprise customers.
This is the external-facing chat interface where users interact with our super assistant. Key functionalities include:
- Vanilla Chatbots: Chatbots that rely solely on user-provided context during conversations
- Custom Chatbots: Developer-tailored Chatbots with specific data, logic, or functionality
- AI Workflows: Custom AI Agents created by developers and exposed to users
- ChatLLM Projects: Consistent workspaces for uploading documents and instructions
- Abacus AI Deep Agent: Our step toward Artificial General Intelligence, featuring app creation, PowerPoint generation, and system integrations
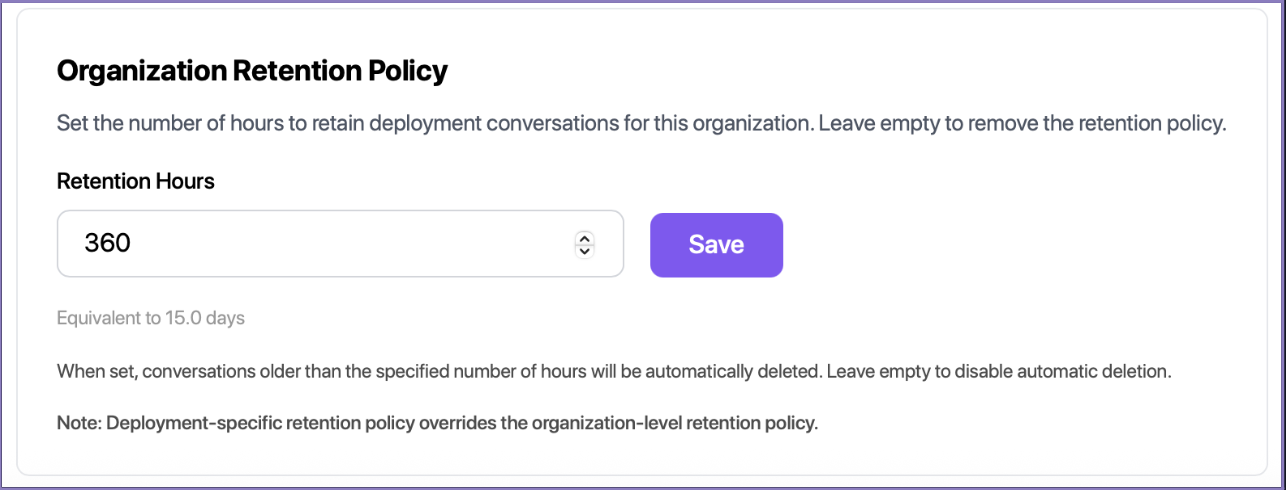
For enterprise customers, Chatbot data is retained within the Abacus platform for 180 days. However, Abacus maintains a strict zero-day retention policy with all external LLM providers—meaning your data is never stored by third-party providers and is never used for model training. Enterprise customers also have the options to change the retention policy of all chatbots within the abacus platform.
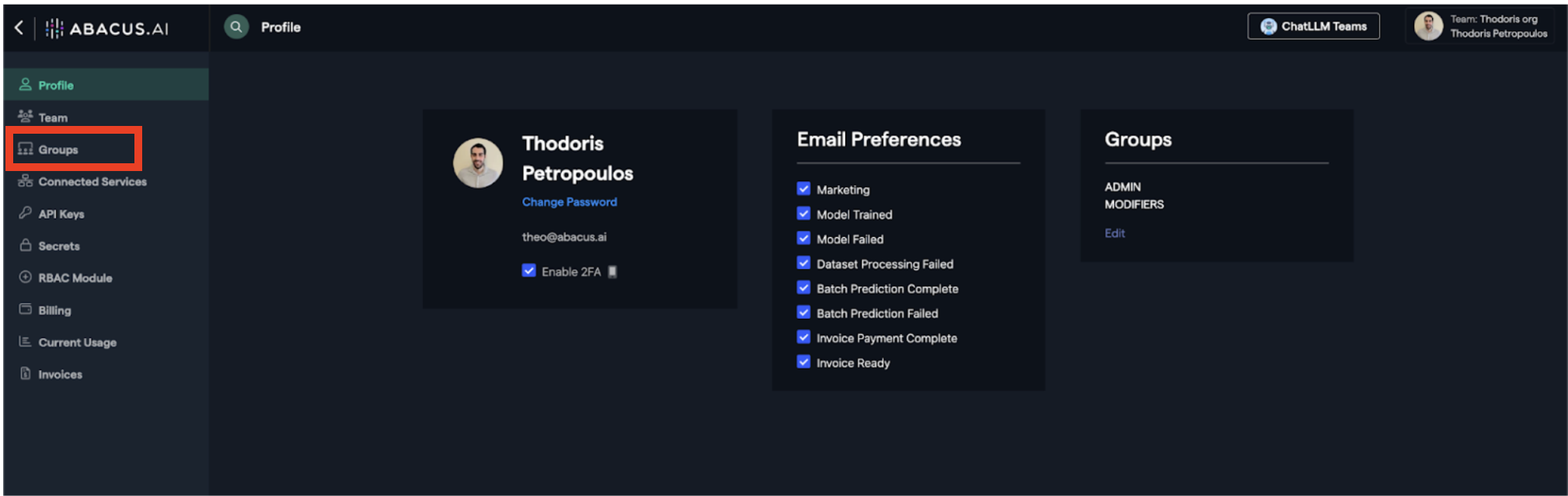
To enable this navigate to the Profile menu by clicking on your profile on the top right-hand corner and selecting profile.
On the Profile page then use the menu on the left to select Manage >> Permissions
User Personas
The platform categorizes users into three main groups, each with distinct access levels and permissions:
1. Organization Admins
- Full access to all resources, connectors, and Chatbots
- Can manage and remove users
2. Platform Users (Developers)
- Default access to all resources, connectors, and Chatbots
- Admins can restrict what access platform users have
- Focus on building and managing Chatbots and integrations
3. External Chat Users
- Access only to external Chatbots assigned to their group
- No access to the backend system or organization-level connectors
Managing Users and Invitations
You can invite users through both the Developers Platform and the External Chat UI.
Inviting from the Developers Platform: Users are automatically assigned the Platform User/Developer role.
Inviting from the External Chat UI: Users are designated as External Chat Users by default.
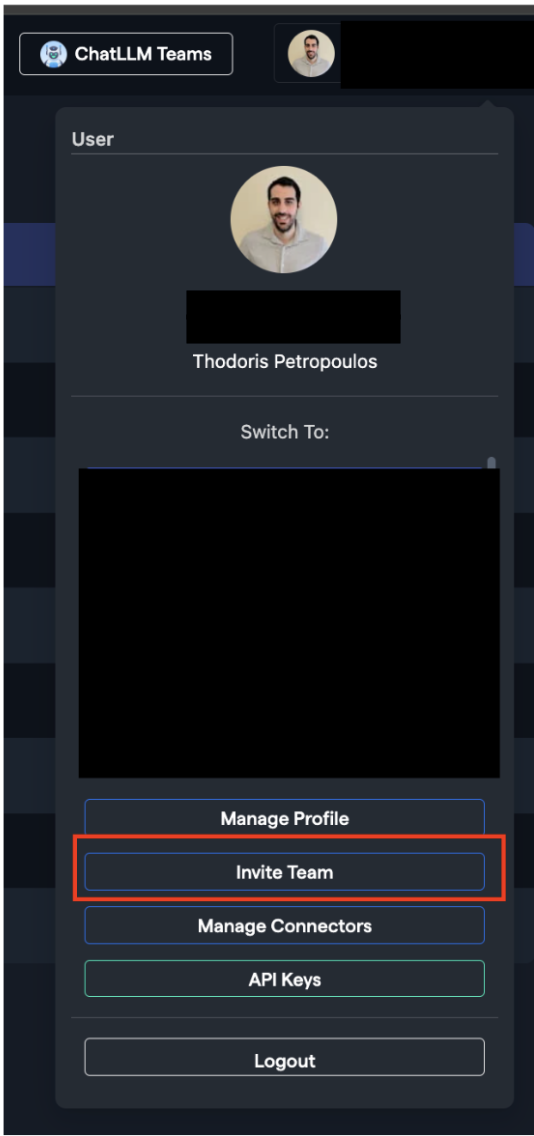
To invite users on either platform, navigate to the top-right corner and click the "Invite Team" button or access the "Team" section through the "Profile" button. "Team" just refers to the users that have access to the particular organization.
Note: Only the External Chat UI allows you to promote or demote users to Platform Users. Organization admins can manage roles using the "Make Platform User" option.
Managing Groups and Access
Abacus.AI allows you to create native groups or manage groups through Azure Active Directory. All instructions below apply to both native Abacus groups and Azure AD groups.
External Chat UI Groups
External Chat UI groups are primarily used to:
- Control access to Custom ChatBots
- By default, custom ChatBots are only available to Platform Users, not External Chat Users
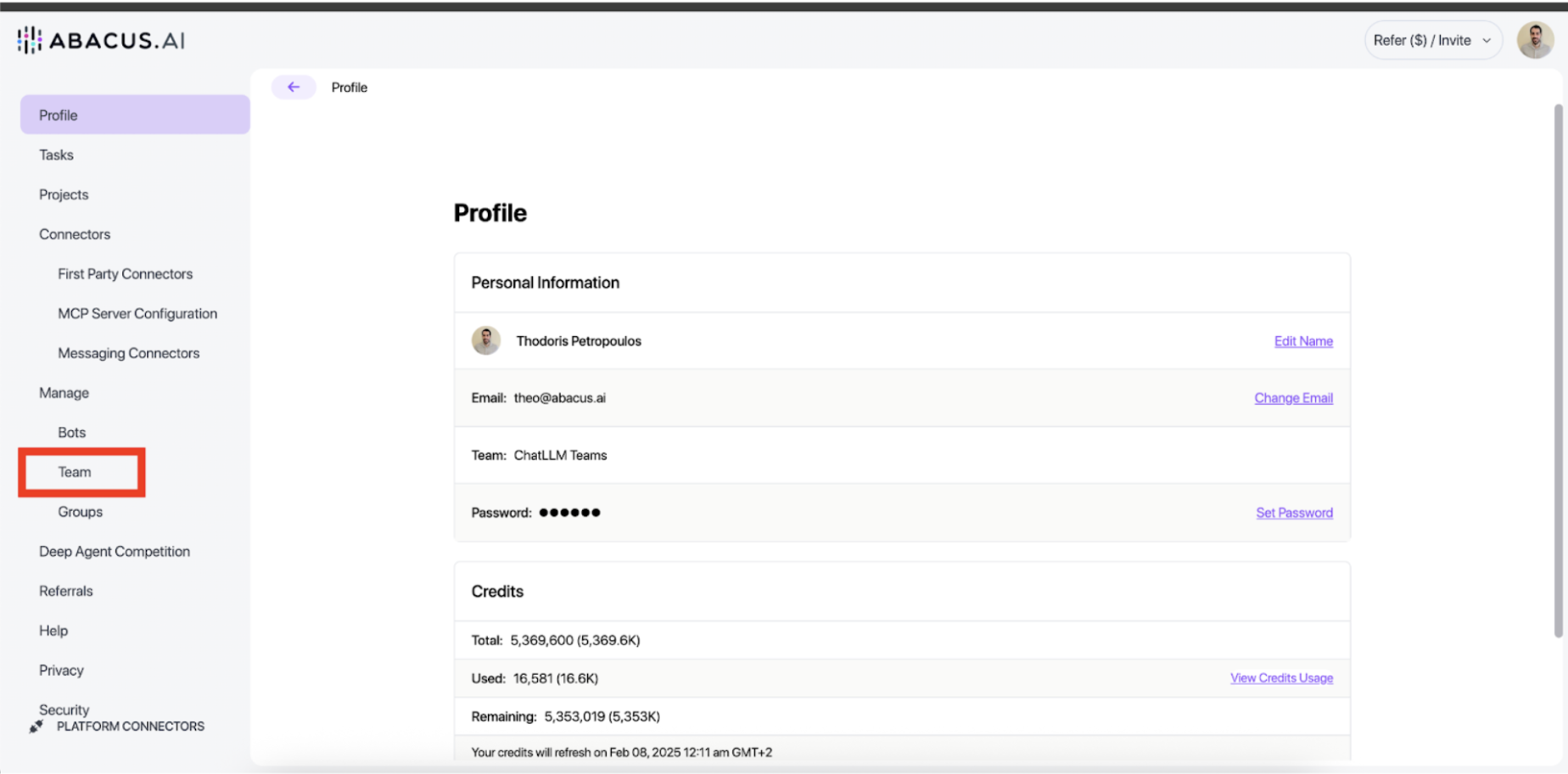
Navigating to User Groups
- Click your user icon in the top right
- Click the "Profile" button
- Click "Groups" on the left side of the UI
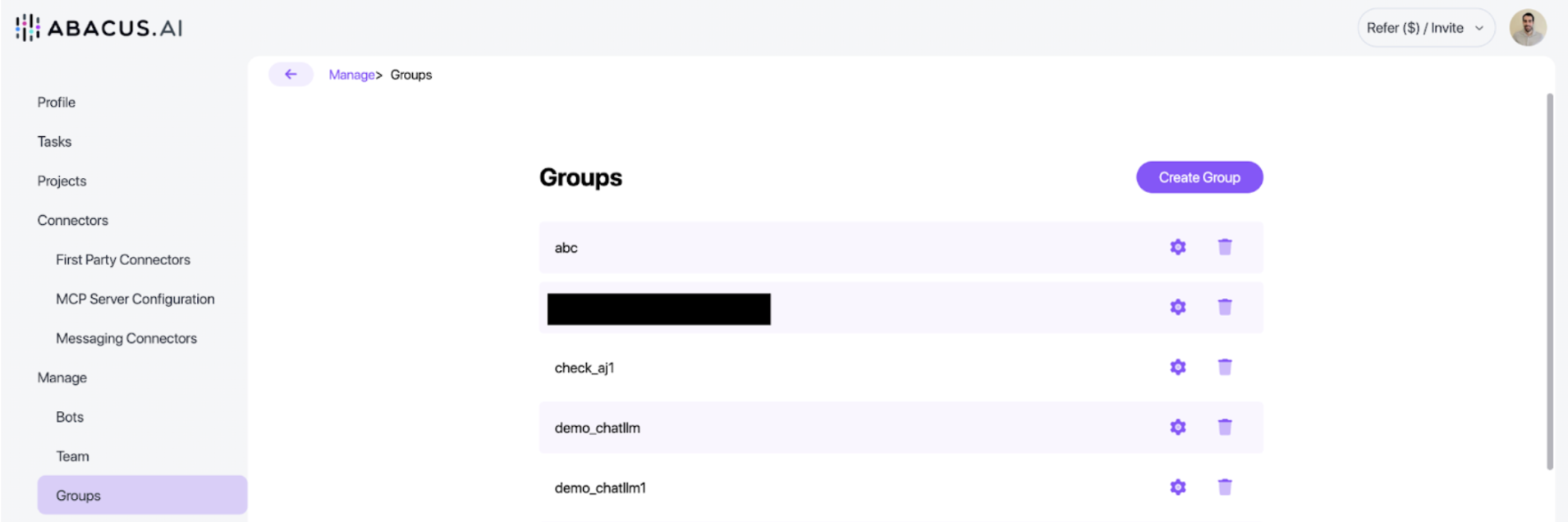
From this interface, you can view all current local Abacus groups. If using AD groups, this page will be empty as we use your AD groups directly. /Users/theo/Desktop/external_chat_groups.png For local groups, add users by clicking the cog icon in the UI.
Managing ChatBot Access
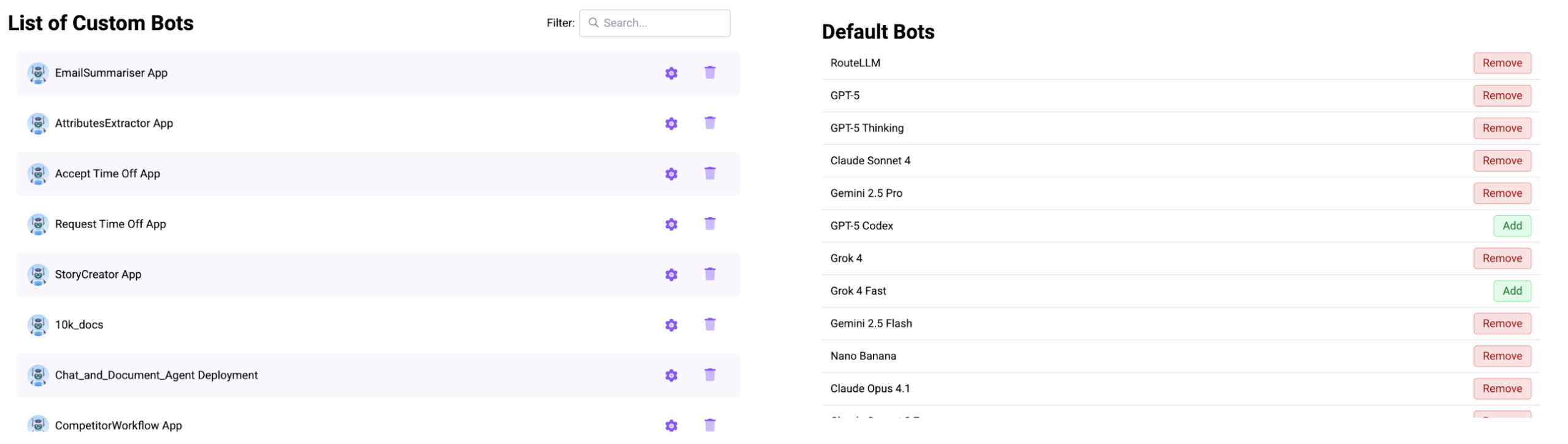
To change who has access to a custom ChatBot, click the "Bots" button from the groups UI. You'll see:
- A list of custom bots
- A list of LLMs available to your organization (admins can disable any vanilla LLM)
Click the cog icon on any custom bot to manage access. Two special groups exist:
- Chat Only Users: External Chat UI users only
- Developers: Platform/Developer users
By default, all Platform Users / Developers can access any created Custom ChatBot (created through the backend system), but access can be revoked to protect sensitive projects. Chat Users never have access to Custom ChatBots unless explicitly granted.
For custom Chatbots, by using the cog icon, you can also alter the UI:
- Add Default prompts
- Add a Banner Message
- Set the retention policy for the particular Custom Chatbot
- Change the icon of the custom Chatbot
Backend Platform Groups and Access Control
Platform Groups are primarily used to:
- Control access to backend projects/use cases
- Control access to connectors
- Control access to datasets
- Assign specific user permissions
Navigating to Groups
- Click "Manage Profile"
- Click "Groups" on the left side panel
From this page, you'll see both local Abacus groups and Active Directory imported groups. For AD groups, users aren't shown here—they should be managed within AD.
Default Permissions
By default, Platform Users are invited into the "MODIFIERS" group with access to all available permissions. However, you can remove users from "MODIFIERS" and add them to any other group, then modify the permissions attached to each group.
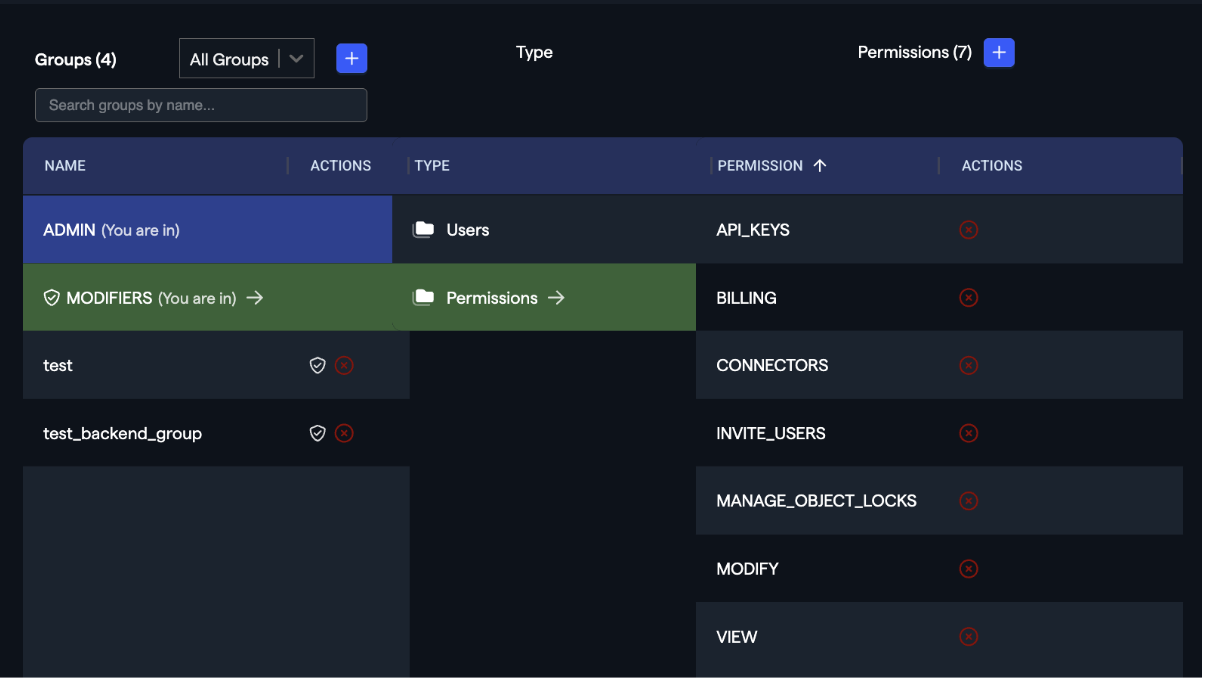
Permission Descriptions
- API_KEYS: Whether users can create and use API keys outside the Abacus platform
- BILLING: Whether users can access the billing dashboard
- CONNECTORS: Ability to create new database and/or application connectors
- INVITE_USERS: Ability to invite users into the platform
- MANAGE_OBJECT_LOCKS: Whether users can use object locks (covered separately)
- MODIFY: Whether users can modify platform elements. Without MODIFY permissions, users cannot:
- Retrain models or alter SQL queries
- Make any changes that would impact Abacus projects
Important: If a user belongs to multiple groups, they inherit the maximum permissions from all groups.
RBAC Module
To restrict access to Abacus objects within the Development platform, navigate to the "RBAC Module" on the left side panel.
From this page, you can control who can see:
- Projects
- Datasets
- Feature Groups
- Connectors
- Secrets
By default, all projects, datasets, connectors, and feature groups are available to all Platform Users. Once you apply a policy stating "Object X is only accessible to user group Y," every other platform user loses access to that particular object type.
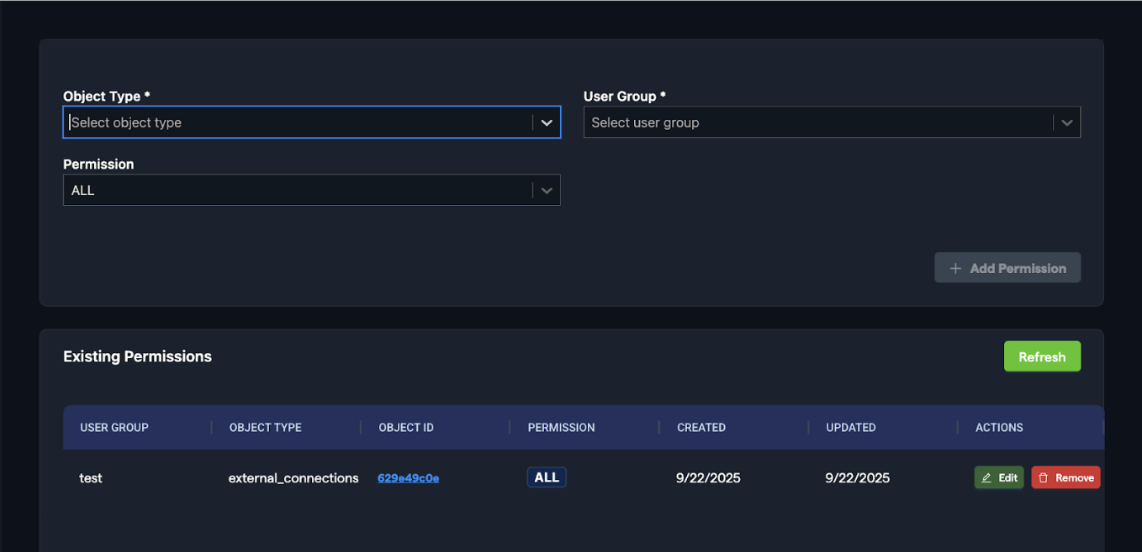
Understanding "ALL" Permissions
Permissions only have an "ALL" option to communicate that the group receiving access to an object (while restricting it for all other groups) will have ALL permissions related to their group.
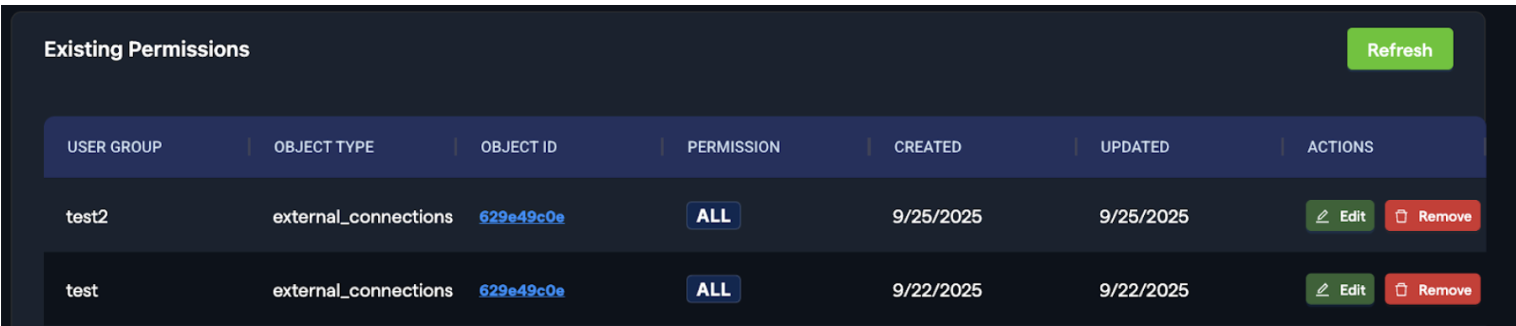
Example
We have two user groups, test2 and test, both with access to object ID: 629349c0e. Below are the permissions assigned to each group:
test2:
- VIEW
test:
- VIEW
- MODIFY
When users from the test group interact with this connection, they can modify it. In contrast, users from the test2 group only have view access and cannot make changes.
These permissions are inherited from group-level permissions. The RBAC Module allows you to define private objects and specify which groups or users have access to them. All permissions for these private objects are inherited from group-level settings.
App Permissions
Abacus AI Deep Agent enables you to create full-fledged applications with flexible access controls.
Permission Levels by Plan
Non-Enterprise Customers
- All deployed apps are public by default
Enterprise Customers
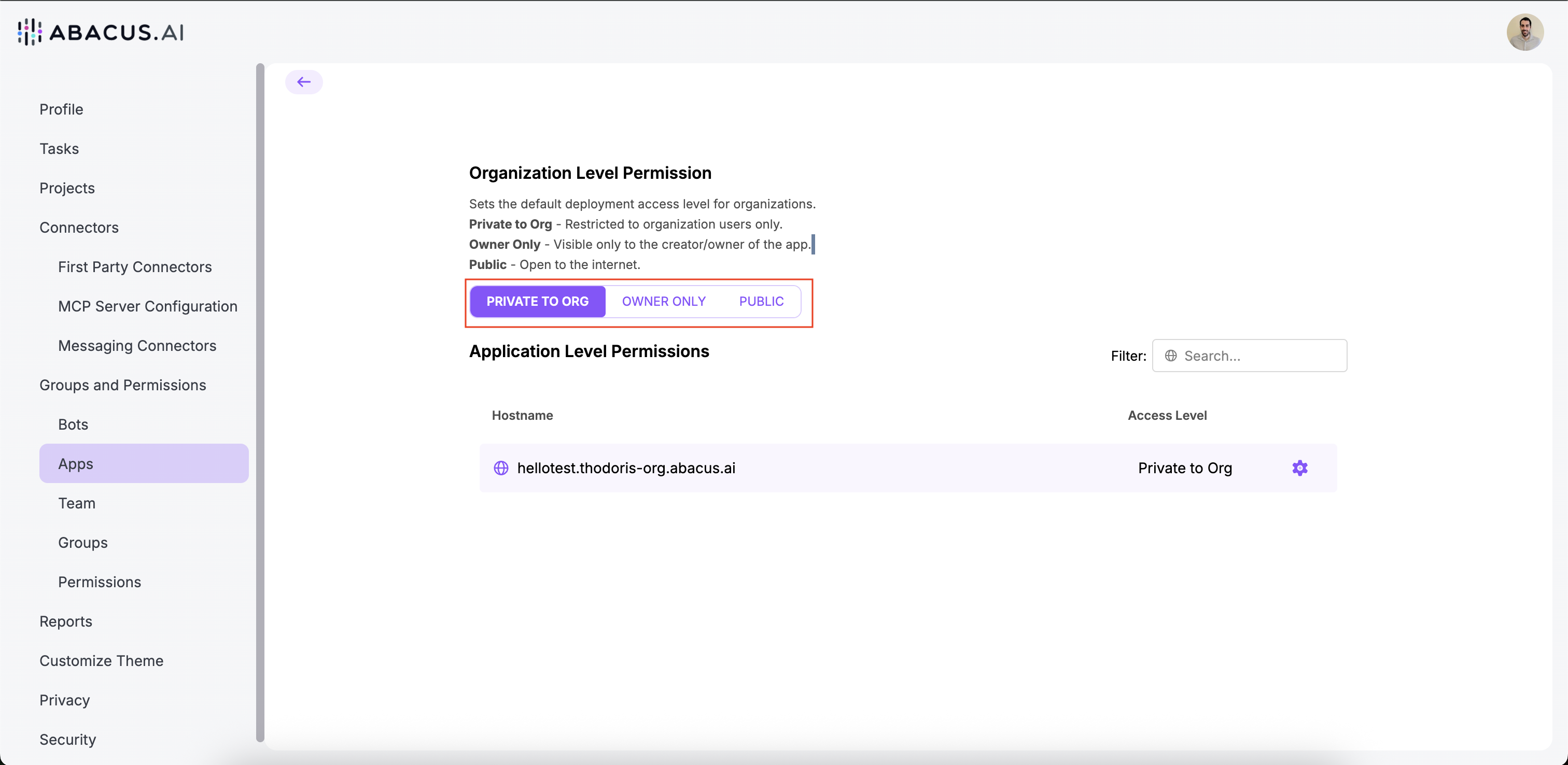
Enterprise customers can choose between:
- Private to ORG: Applications are only available to the particular organization (protected under SSO).
- Public: Available to the internet
- Owner Only: Available only to the owner of the application.
The default settings of application deployment can be modified only by organization admins within this page: https://your-workspace.abacus.ai/chatllm/admin/apps/
To navigate there:
- Click on Profile (on the top right page where you see your account icon)
- Click on "Apps" on the left side panel
From this page you can choose whether an application is "Private to ORG", "Public", or "Owner Only" by default. This will apply to all users once they try to deploy an application.
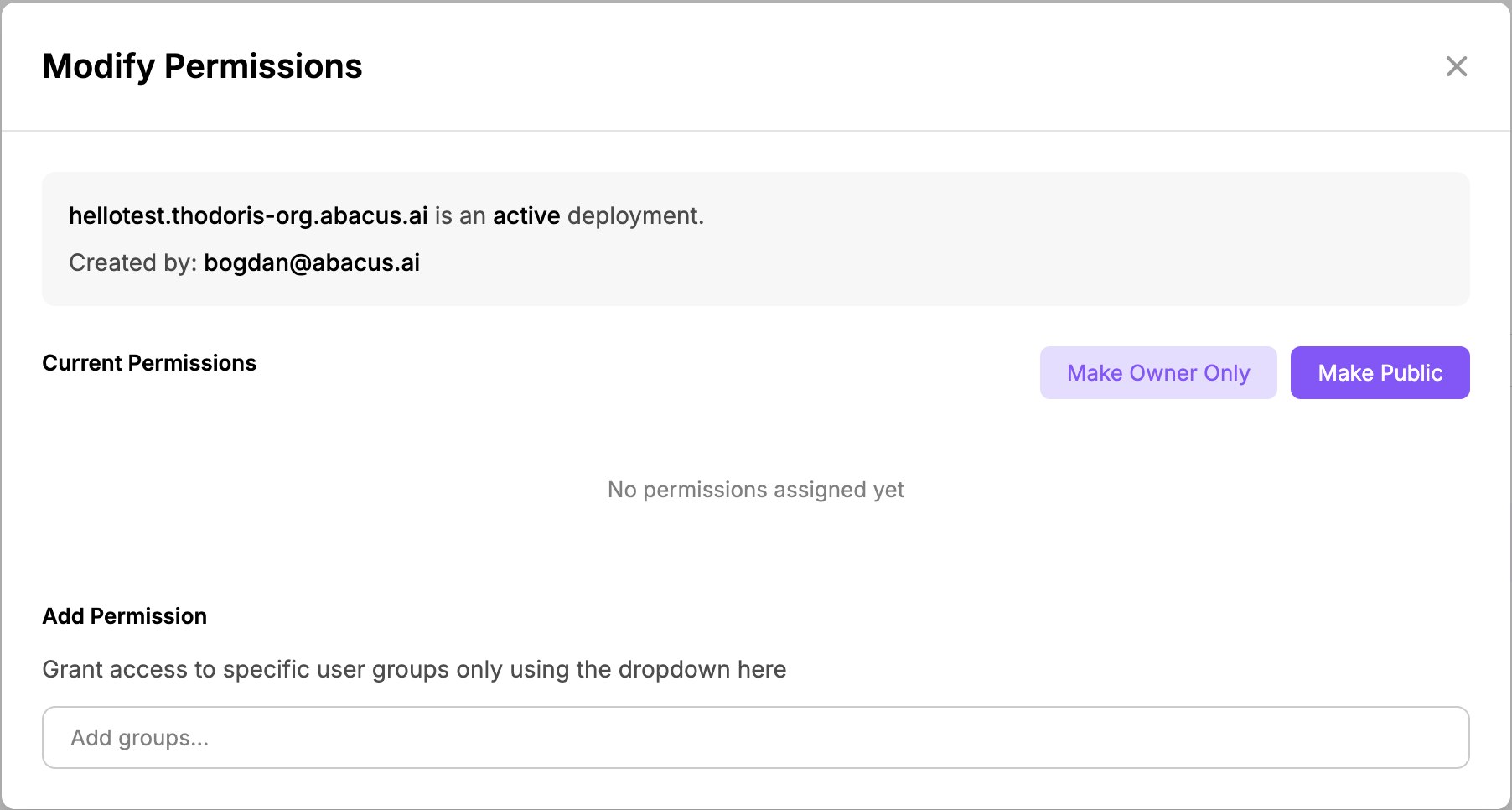
By clicking on the cog icon of a specific deployed application, you can also:
- Share a deployed app with a specific group of Users (Owner of app and Organization Admins)
- Change whether a specific app is "Private to ORG", "Public" or "Owner Only" (Organization Admins Only)
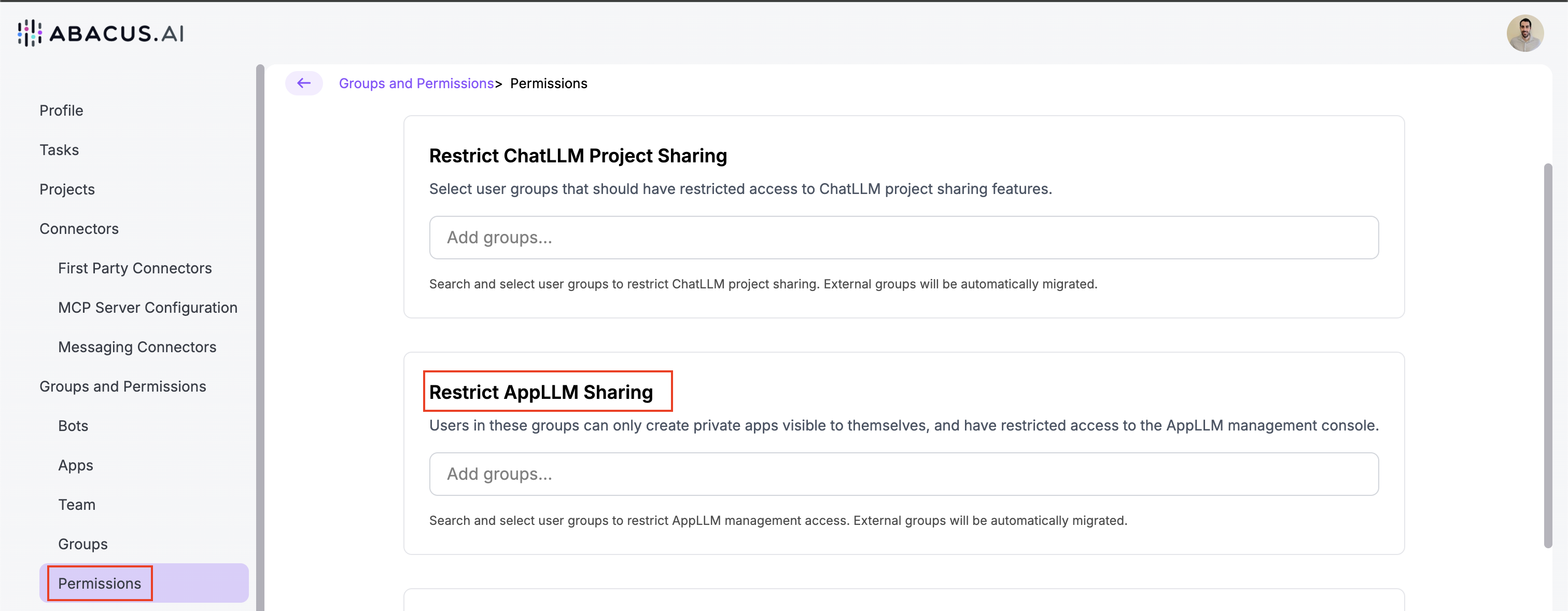
Restricting App Sharing
This functionality is also available only to enterprise customers.
From this dashboard: https://your-workspace.abacus.ai/chatllm/admin/permissions/, organization admins can restrict who can actually share applications.
Regardless of the default settings for applications in the organization, for groups that are restricted this means:
- They won't be able to share the application to specific groups of users
- All applications they create will be "Owner Only"
This is useful for non technical users that create applications and IT teams that want to audit before sharing with the wider organization.
Throttling
From the same dashboard: https://your-workspace.abacus.ai/chatllm/admin/permissions/, organization admins that use our enterprise plan can also throttle the usage either globally per user or per group of users.
Please note that the throttling is on a user level and a 24 hour window. Users who exceed their limit will be blocked until the quota resets at 2pm UTC daily.
Logging and Usage Metrics
Abacus provides a comprehensive Dataset with all interactions of users with our platform. To set it up, please follow the instructions here: https://abacus.ai/help/connectors/applicationConnectors/abacus_usage_metrics
This is a SQL table that will host all interactions people are having with the system. It can also be exported to the system of your choice, if you so wish to. Here is the available information:
deployment_conversation_idchatbot_namenum_messagesconversation_historyconversation_updated_atfiles_usedfirst_messagedeployment_idlast_feedbacksourcenum_positive_feedbackconversation_urlemailproject_idfeedback_categorieslast_feedback_typelast_message_sent_atconversation_created_atnum_negative_feedbackdoc_referenced
You can easily monitor your usage with our comprehensive dashboard, which provides clear insights at both the user and project levels. Access the dashboard here: https://abacus.ai/app/profile/usage. It offers a transparent view of your token consumption, and you'll find per-user usage details conveniently displayed in the top right corner.
If you wish to monitor usage via an API, there is an api method you can use - please contact your Abacus representative for details.
QA, Stage, and Production Environment
When setting up Stage and Production environments, there are multiple approaches you can take. While it is possible to create two completely separate environments or organizations, this is not the recommended method. Instead, leveraging the platform's built-in tools to manage DEV and PROD versions is a more efficient and streamlined approach.
Recommended Approach: Using Built-In Tools
The platform provides two key objects to manage environments effectively:
- Deployments
- Models
Deployments are designed to be completely standalone and highly flexible. They can connect to any model, allowing you to make changes seamlessly. For instance, you can update a PROD deployment to connect to a different model or even a different version of the same model. This flexibility ensures that you can manage your environments without duplicating efforts or creating unnecessary complexity.
You can learn more about deployments here.
Furthermore, you can set up GitHub CI/CD pipelines to push updates to the platform. All of our objects have APIs that can be used to retrain models, update AI Workflows (AI Agents), and any object within the platform.
In summary, the platform is flexible enough to allow you to work within your own IT standards, but using the platform's built-in tools has many productivity benefits.
Strategies to Reduce LLM Costs
If you're concerned about managing LLM costs for your organization, there are several effective strategies you can implement to optimize expenses without compromising performance:
Disable Expensive Models
Restrict the use of high-cost models unless absolutely necessary. This ensures that resources are allocated efficiently and only where they add the most value.
Optimize Context Size for Custom Bots
Reduce the context size window by limiting the number of search results or data points fed into the model. This not only lowers costs but also improves processing speed.
Control Access to Expensive Models
Grant access to premium models only to developers or teams who truly need them for critical tasks. For everyone else, provide access to more cost-effective options, such as smaller or less resource-intensive models.
Leverage RouteLLM for Cost Optimization
Use tools like RouteLLM, which are specifically designed to optimize for cost while maintaining performance. By standardizing on RouteLLM, you can eliminate unnecessary LLM options and streamline your operations.
By implementing these strategies, your organization can significantly reduce LLM-related expenses while maintaining efficiency and effectiveness in your AI-driven workflows.