Connect Your Microsoft Entra ID Active Directory to Abacus.AI
This guide details how to integrate Microsoft Entra ID with Abacus.AI for user management.
- Overview
- Requirements
- Setting up the Microsoft Entra ID connector
- Required Permissions
- Managing users and groups
- Licenses
- Using the Microsoft Entra Connector
- Troubleshooting and FAQ
Overview
This document outlines the setup process for integrating Microsoft Entra ID (formerly Azure AD) with Abacus.AI for user management and Single Sign-On (SSO). It also includes best practices, security requirements, and answers to commonly asked enterprise questions. For SAML-based instructions, please see the instructions here.
Requirements
- Have the appropriate Microsoft licenses:
- Microsoft Entra ID P2 (required)
- Microsoft Entra ID Governance (recommended)
- Both licenses are necessary in order to assign Microsoft users and groups to Abacus.AI roles
- Set the proper permissions in Microsoft Entra ID
- Create the Microsoft Entra ID authentication connector on the Abacus.AI platform
- Reach out to Abacus.AI to set the specified organization's managed user service to Microsoft
- Ensure all users are assigned roles in Microsoft Entra ID before switching managed user services.
- Existing users who are not properly migrated may lose access.
- Contact your Abacus representative to complete the final step of switching to Microsoft Entra ID as your managed service.
Setting up the Microsoft Entra ID connector
-
While logged out of the Abacus.AI platform, click on "Sign in with Microsoft" to install the Abacus.AI app into your Microsoft Entra tenant. Make sure that it’s the enterprise version
<workspace>.abacus.ai. -
Log into your Microsoft Entra admin dashboard
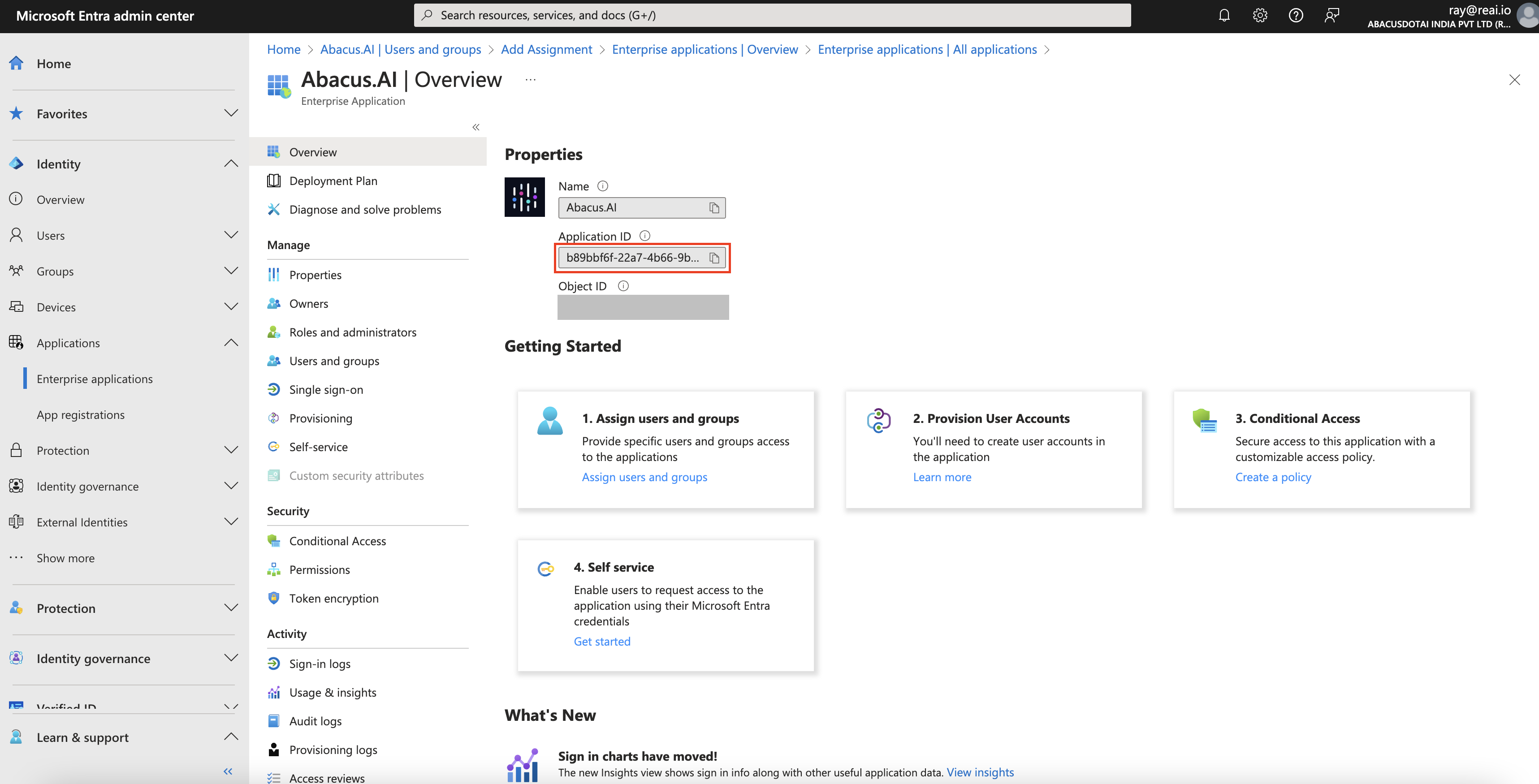
- Go to the Enterprise applications tab and select the installation of Abacus.AI with Application ID: b89bbf6f-22a7-4b66-9bcf-6a80edf04dc5.
- Go to the permissions tab and ensure the following permissions are enabled:
Required Microsoft Graph Permissions
| Permission | Description | Needed for SSO |
|---|---|---|
| Application.Read.All | Read applications | No |
| Directory.Read.All | Read directory data | No |
| View users' email address | Yes | |
| offline_access | Maintain access to data you have given it access | Yes |
| openid | Sign users in | Yes |
| profile | View users' basic profile | Yes |
| User.Read | Sign in and read user profile | Yes |
| User.ReadBasic.All | Read all users' basic profiles | Yes |
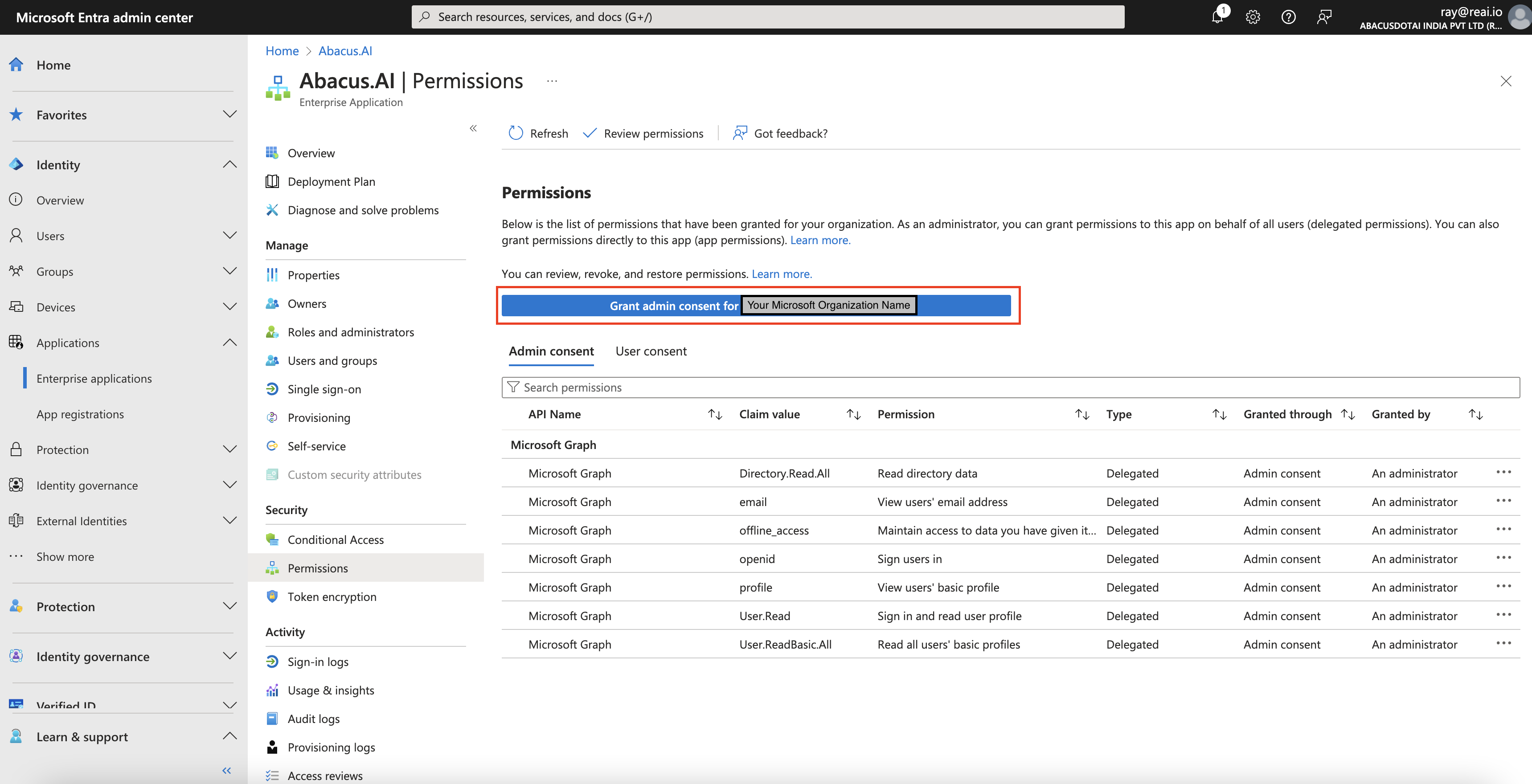
If not already there, you may have to click the "Grant admin consent" button first. The above screenshot is from after granting admin consent.
- Follow the pop-up instructions accordingly (Microsoft admin permissions are necessary).
Managing accounts on Microsoft Entra ID:
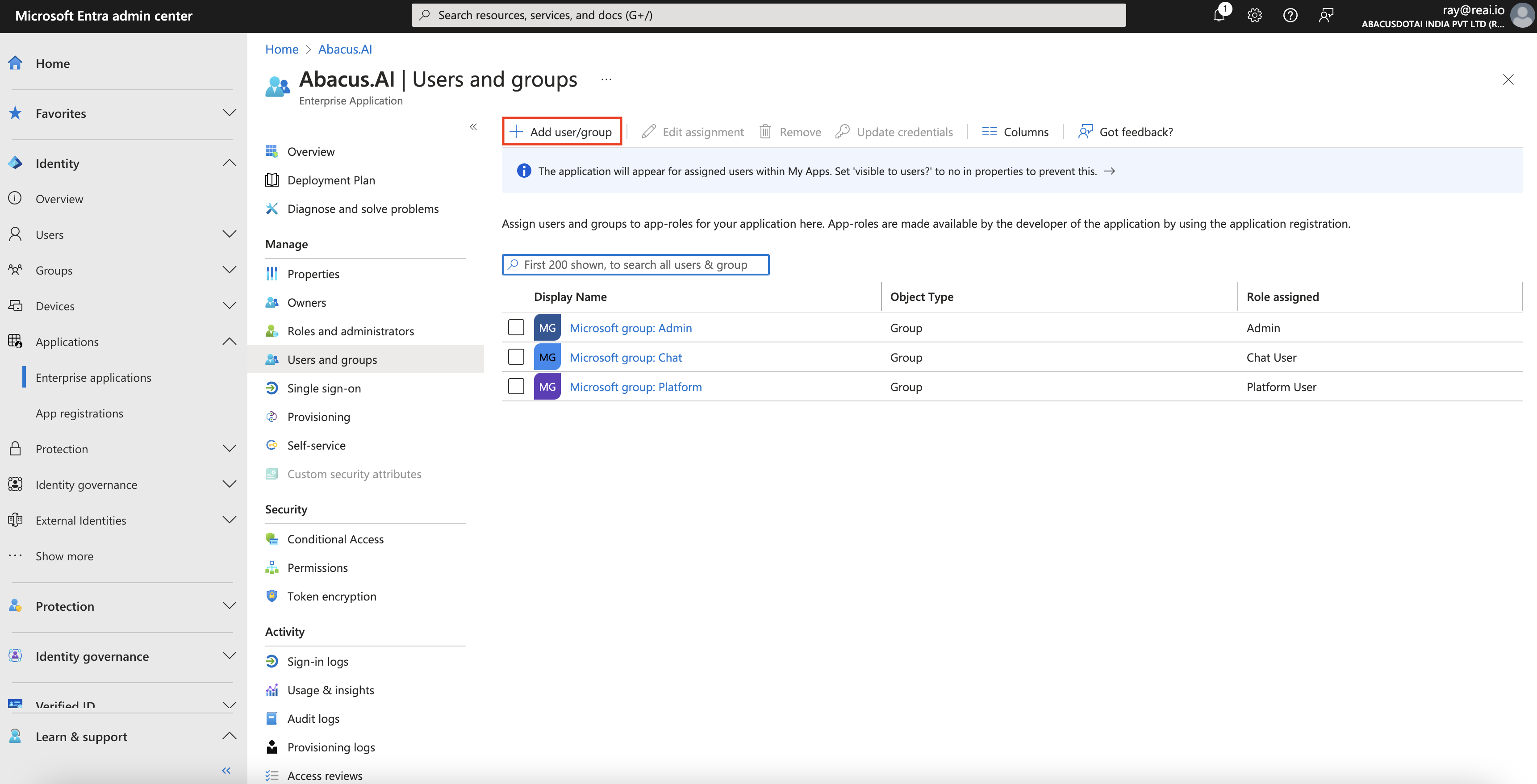
- Go to the "Users and groups" tab and press "Add user/group".
-
Select the users or groups you want to give access to, along with their corresponding roles:
-
Admin - The user is an admin on the Abacus.AI Chat and platform.
-
Chat User - The user only has access to the Abacus.AI Chat.
-
Platform User - The user has access to the Abacus.AI Chat and platform.
-
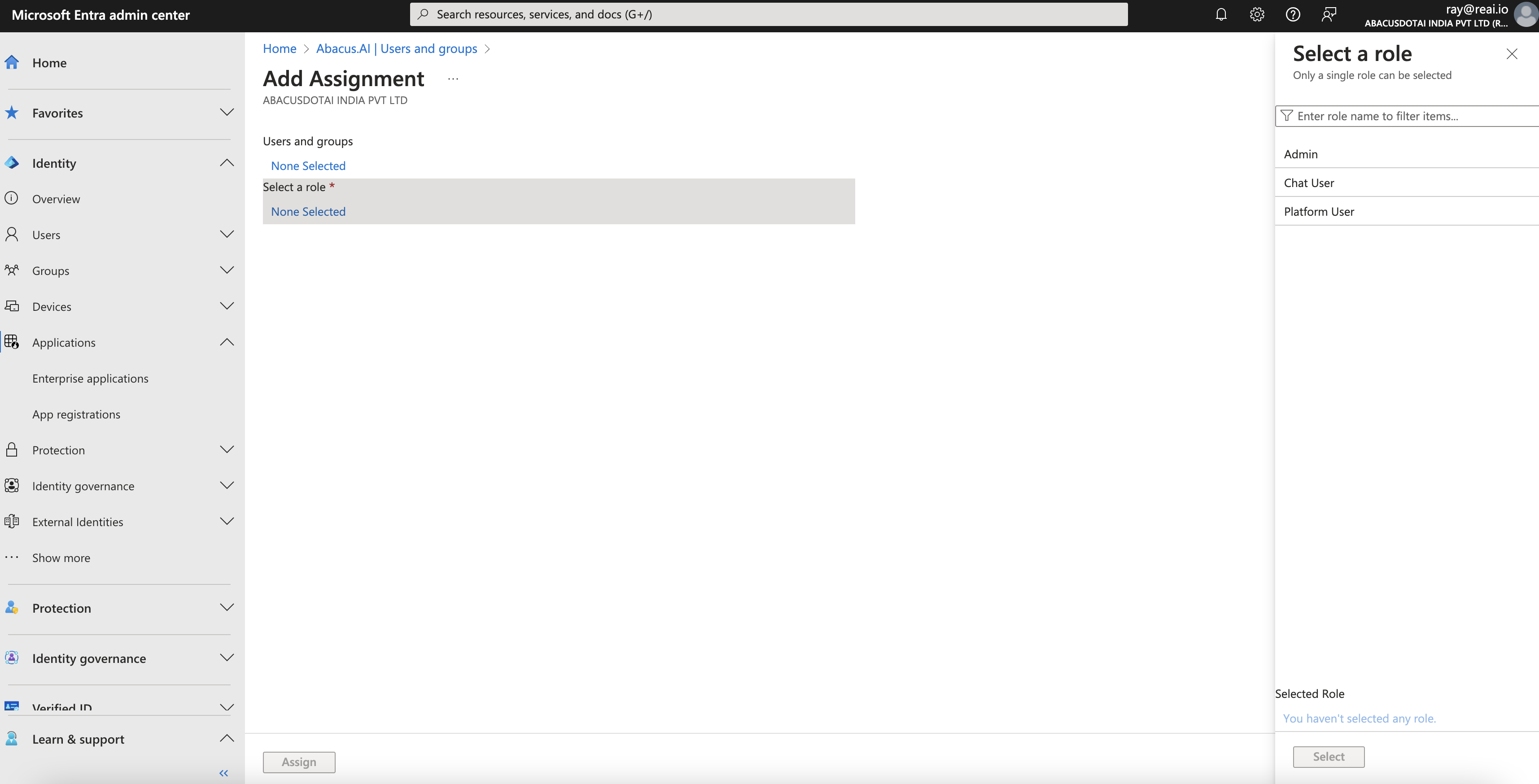
Licenses
While Microsoft Entra ID Governance is not strictly necessary for single sign-on (SSO) integration, it becomes essential when you want to leverage group-based role assignments and automated identity management features as group assignments are not avalailable from Microsoft without this plan.
Your team can still use SSO integration if you're willing to accept the limitations of manually assigning roles to individual users. However, if you want to assign roles to user groups and enable access to private group-specific bots for "Chat Users," then Entra ID Governance is necessary, but only 1-2 licenses would be needed for the admins who will manage and maintain the groups.
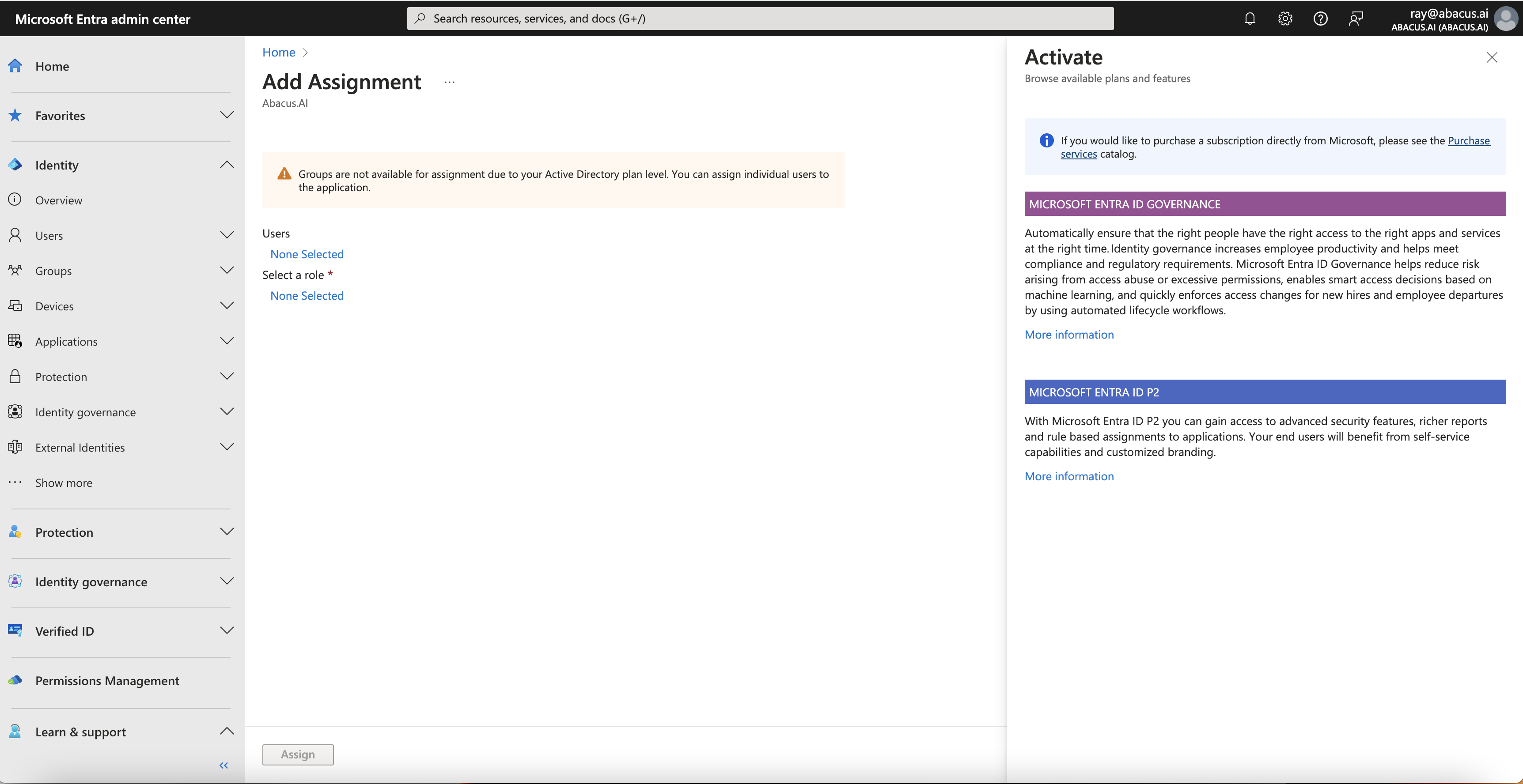
The Microsoft Entra ID P2 license is mandatory for integration with Abacus.AI. It is required to enable critical features such as Dynamic Group Management, which allows you to assign roles to user groups instead of individual users. This is essential for managing access efficiently in larger organizations. Additionally, without a P2 license, certain third-party applications (like Abacus.AI) may not appear in the Enterprise Applications section of Microsoft Entra ID, as the license unlocks advanced application visibility and management capabilities.
The P2 license also provides Advanced Security Features like Conditional Access, Identity Protection, and Privileged Identity Management (PIM), ensuring secure access to Abacus.AI. It enables Directory and Application Permissions, allowing seamless management of directory data and role assignments. Furthermore, it includes compliance tools like Access Reviews, which are critical for maintaining governance and periodically validating user access.
-
Without the P2 license, you will not be able to:
- Assign roles to groups (manual user role assignment would be required).
- Fully integrate Abacus.AI with Microsoft Entra ID for automated identity management.
Using the Microsoft Entra ID connector
If your team only wants SSO login, then you can stop here. However, if you also want to manage groups for your chatbot, please continue.
- Select Organization:
- Go to the organization that you want to be managed by Microsoft Entra ID.
-
Access Connected Services Dashboard:
- Go to the Abacus.AI Connected Services Dashboard. You can click your profile in the top right and then click "Manage Connectors".
-
Add New Connector:
- Click on the "Add New Connector" option and select "Microsoft Entra ID".
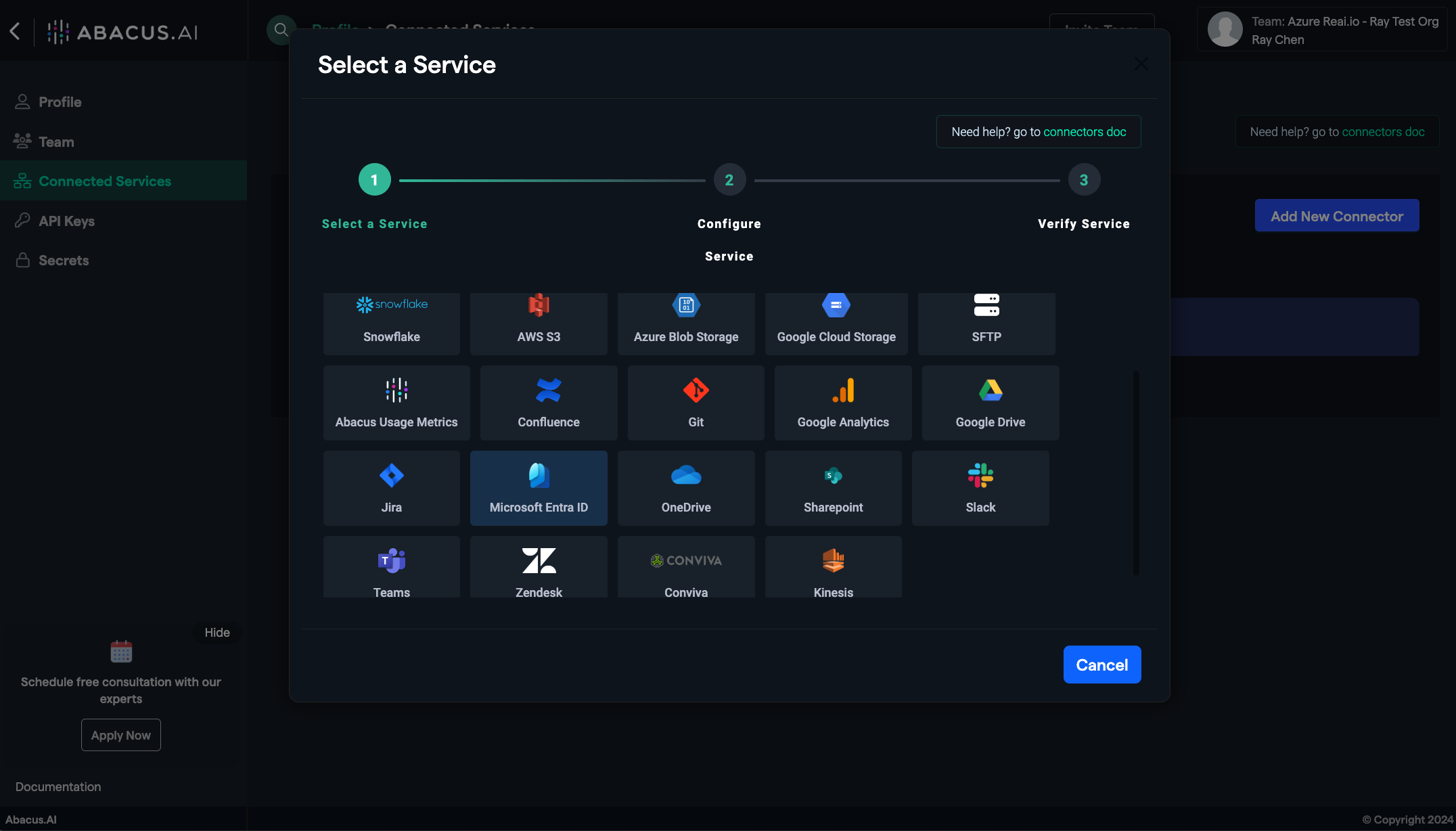
- Connect Microsoft Entra ID:
- Press the "Connect Microsoft Entra ID" button. Follow the instructions in the dialog box to provide your Microsoft admin user credentials -- the account that has your target directory as the home organization.
- Ensure you have granted admin consent as outlined
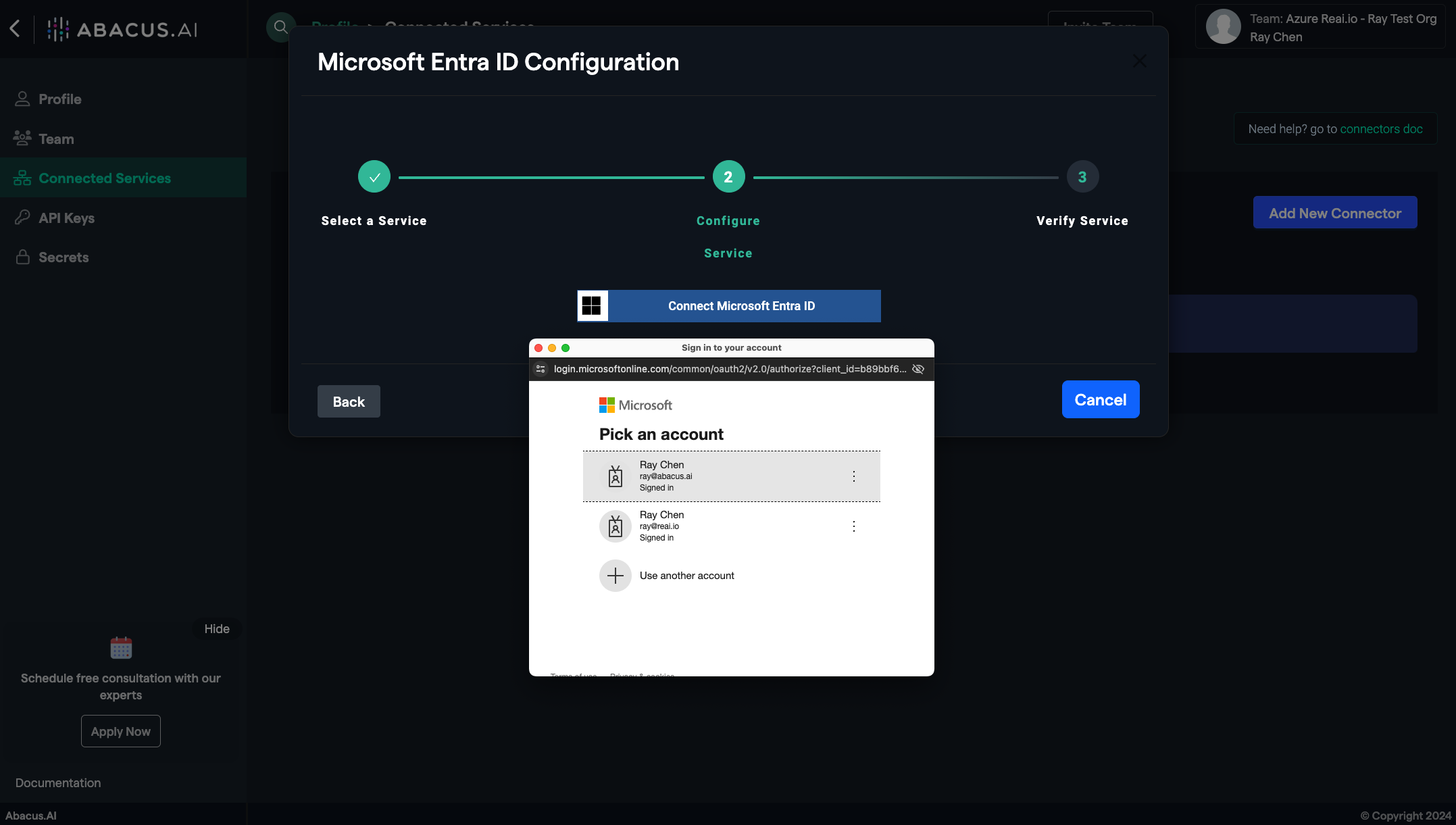
-
Verify Connector Status:
- Your connector should be set up and confirm that it has an "ACTIVE" status.
-
Enable Feature:
- Reach out to Abacus.AI to enable this feature and have Microsoft Entra ID manage user accounts for this organization.
Note:
- New users will be automatically created in Abacus.AI when they log in for the first time.
- Please note that existing users (emails already associated with another Abacus.AI organization) will not be added to the new organization upon login.
- In such cases, you will need to explicitly invite existing users to the new organization.
- Ensure that the email domain used for login is not already associated with another Abacus.AI organization, as this may cause conflicts.
Troubleshooting and FAQ for the Microsoft Entra ID connector
- On Microsoft, users must be internal members and not guests. The emails should be of the form
@domain.com, notext@domain-on-microsoft.com - When logging into the
https://workspace.abacus.ai/chatllmapplication using Microsoft SSO, the user must switch their Microsoft organization to their targeted directory.